Wireshark is an open source software project and you can freely use Wireshark on any number of computers you like, without worrying about license keys or fees or such.
All source code is freely available under the GPL. Because of that, it is very easy for people to add new protocols to Wireshark, either as plugins, or built into the source, and they often do!
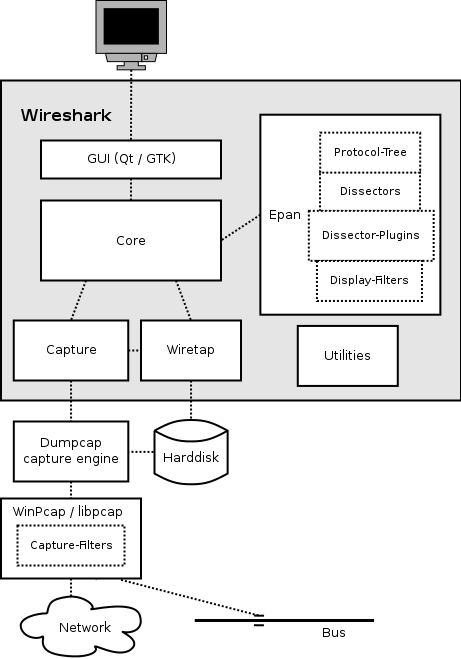
The function blocks in more detail:
GUI
Handling of all user input/output (all windows, dialogs and such). Source code can be found in the ui/qt directory.
Core
Main “glue code” that holds the other blocks together. Source code can be found in the root directory.
Epan
Enhanced Packet Analyzer—the packet-analyzing engine. Source code can be found in the epan directory.
Epan provides the following APIs:
- Protocol Tree – Dissection information for an individual packet.
- Dissectors – The various protocol dissectors in epan/dissectors.
- Dissector Plugins – Support for implementing dissectors as separate modules. Source code can be found in plugins.
- Display Filters – The display filter engine at epan/dfilter.
Wiretap
The wiretap library is used to read and write capture files in libpcap, pcapng, and many other file formats.
Capture
The interface with the capture engine.
Dumpcap
The capture engine itself. This is the only part that is to execute with elevated privileges.
Npcap and libpcap
These are separate libraries that provide packet capture and filtering support on different platforms. The filtering in Npcap and libpcap works at a much lower level than Wireshark’s display filters and uses a significantly different mechanism. That’s why we have different display and capture filter syntaxes.
Capturing packets
Capturing takes packets from a network adapter and saves them to a file on your hard disk.
Since raw network adapter access requires elevated privileges these functions are isolated into the dumpcapprogram. It’s only this program that needs these privileges, allowing the main part of the code (dissectors, user interface, etc) to run with normal user privileges.
To hide all the low-level machine dependent details from Wireshark, the libpcap and Npcap libraries are used. These libraries provide a general-purpose interface to capture packets and are used by a wide variety of applications.
Capture Files
Wireshark can read and write capture files in its natural file formats, pcapng and pcap, which are used by many other network capturing tools, such as tcpdump. In addition to this, as one of its strengths, Wireshark can read and write files in many different file formats of other network capturing tools.
Dissect packets
While Wireshark is loading packets from a file each packet is dissected. Wireshark tries to detect the packet type and gets as much information from the packet as possible. In this run though, only the information shown in the packet list pane is needed.
As the user selects a specific packet in the packet list pane this packet will be dissected again. This time, Wireshark tries to get every single piece of information and put it into the packet details pane.
Also Read- Wireshark Commands Cheatsheet
To get a quick peek in what and how Wireshark works these are the steps.
How we can Capture the Packets?
After downloading and installing Wireshark, you can launch it and double-click the name of a network interface under Capture to start capturing packets on that interface.
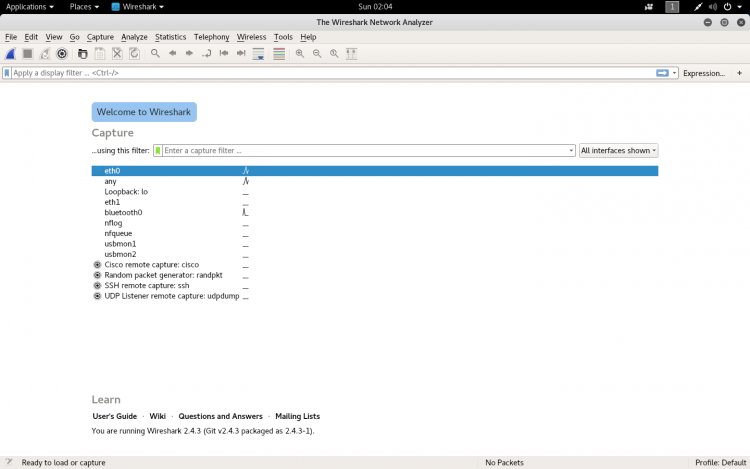
As soon as you click the interface’s name, you’ll see the packets start to appear in real time.
Wireshark captures each packet sent to or from your system.
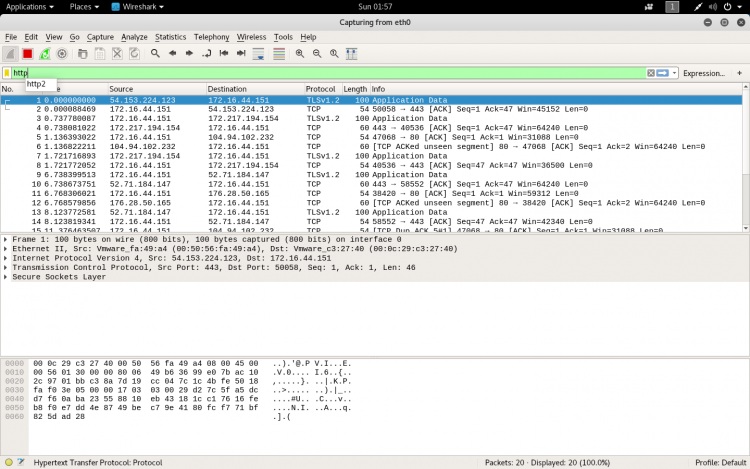
Sometimes the traffics are colour coded to help to identify the types of traffic at a glance. By default, light purple is TCP traffic, light blue is UDP traffic, and black identifies packets with errors.
Also Read- Learn TCP/IP
How we can filter the packets?
If you’re trying to inspect something specific, we filter the packets. The most basic way to apply a filter is by typing it into the filter box at the top of the window and clicking Apply (or pressing Enter).
For example, type “dns” and you’ll see only DNS packets. When you start typing, Wireshark will help you autocomplete your filter.
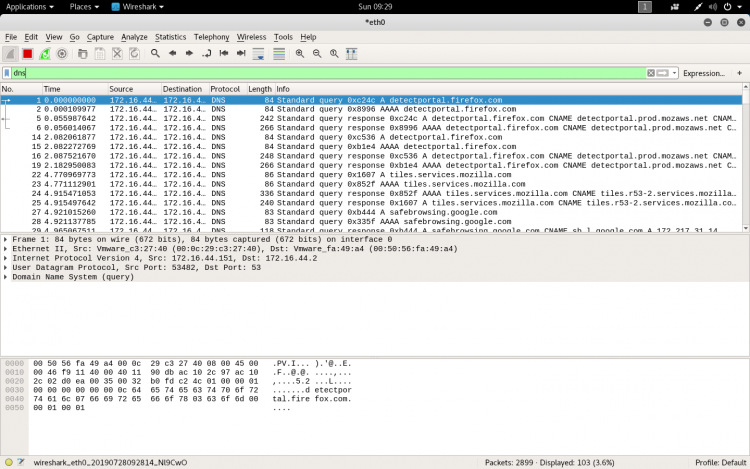
You can also click Analyze > Display Filters to choose a filter from among the default filters included in Wireshark.
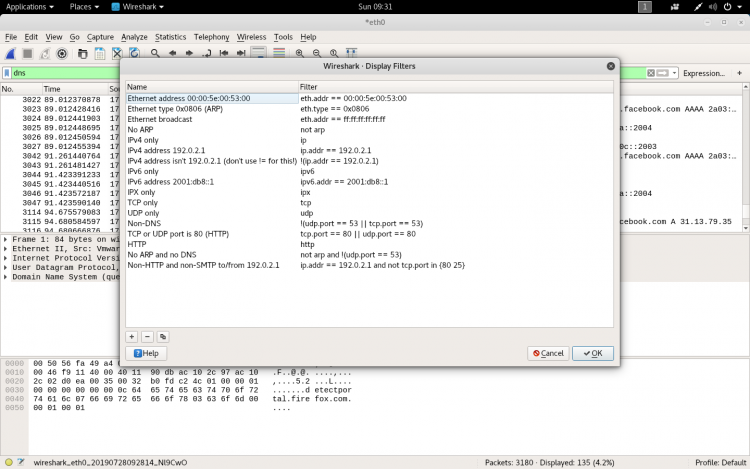
How to inspect the packets?
Click a packet to select it and you can dig down to view its details.
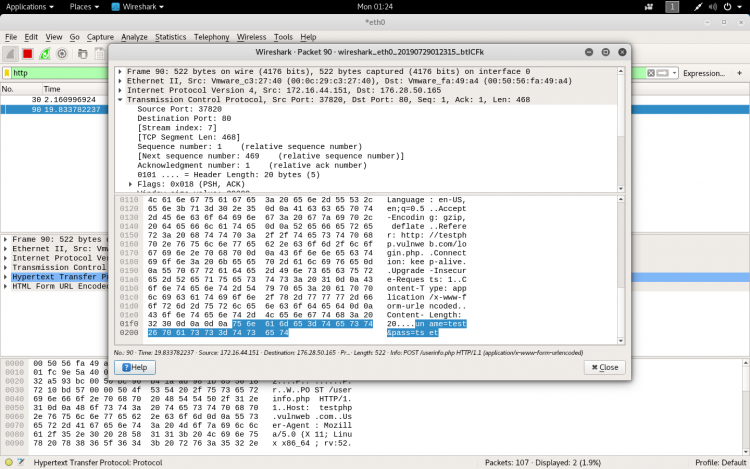
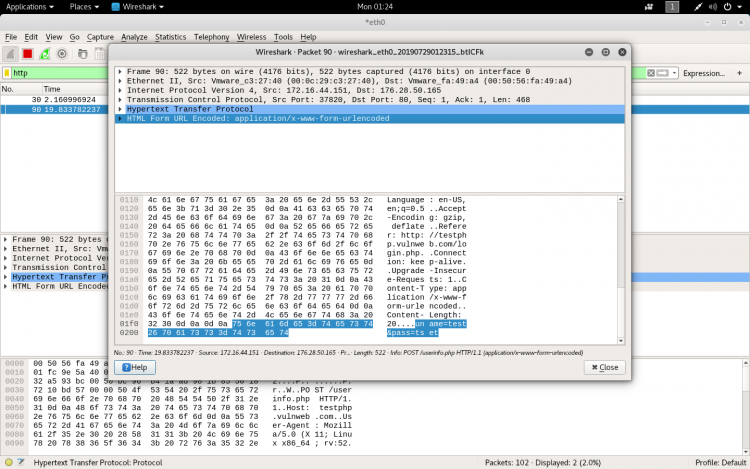
If the site is not secure we can even see the username and password also.
Wireshark is an extremely powerful software, and this tutorial is just scratching the surface of what you can do with it. Professionals use it to debug network protocol implementations, examine security problems and inspect network protocol internals.
Also Read : How To Capture PCAP Logs With Wireshark