Today, we are publishing about Zenmap, a Free Open Source Information Gathering software, which is the graphical user interface of Nmap.
What is Zenmap?
Zenmap is an free and open source GUI for Nmap. It is available on many operating systems (Linux, Windows, Mac OS X, BSD, etc.) Nmap is used to gather information about any device.
Using the Nmap, we can gather information about any client that is within our network or outside our network, and we can gather information about clients just by knowing their IP.
Nmap can be used to bypass firewalls, as well as all kinds of protection and security measures.
Some features of Zenmap
- Easy of use
- Repeatable
- Comparison
- Interactive and graphical result viewing
Also See- How To Use NMAP- A Valuable Open Source Network Security Scanner
So let’s start…
Zenmap is installed in kali linux by default.
Go to Application > Information Gathering > Zenmap
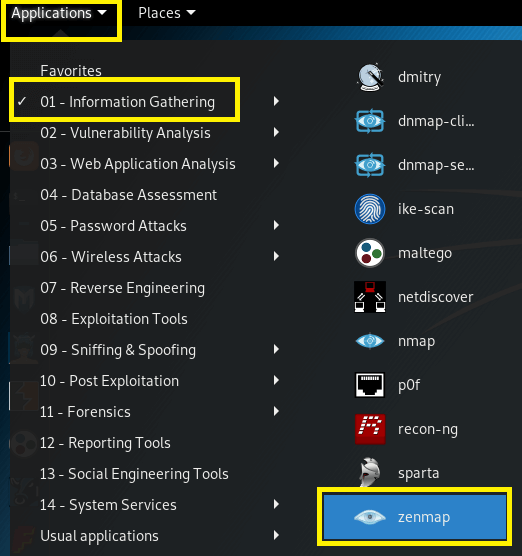
Or we can type zenmap on the Terminal.
In the Target field, we’re going to put IP address or Domain . In the Profile drop-down menu, we can have various profiles:
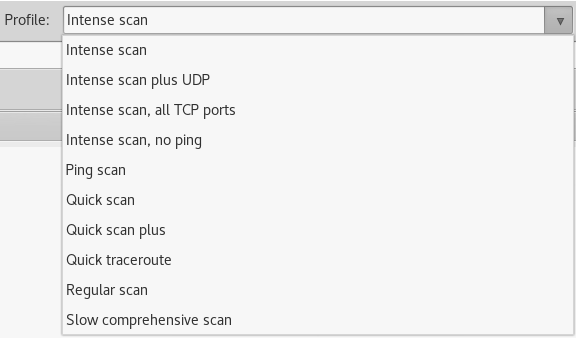
Intense scan
Command: nmap -T4 -A -v <target>
Should be reasonable quick, scan the most common TCP ports. It will make an effort in determining the OS type and what services and their versions are running.
It comes from having a pretty fast timing command (-T4) and for using the -A option which will try determine services, versions and OS. With the verbose output (-v) it will also give us a lot of feedback as Nmap makes progress in the scan.
Intense scan plus UDP
Command: nmap -sS -sU -T4 -A -v <target>
Same as the regular Intense scan, just that we will also scan UDP ports (-sU).
The -sS option is telling Nmap that it should also scan TCP ports using SYN packets. Because this scan includes UDP ports this explicit definition of -sS is necessary.
Intense scan, all TCP ports
Command: nmap -p 1-65535 -T4 -A -v <target>
Normally Nmap scans a list of 1000 most common protocols, but instead we will in this example scan everything from port 1 to 65535 (max). The 1000 most common protocols listing can be found in the file called nmap-services.
Intense scan, no ping
Command: nmap -T4 -A -v -Pn <target>
Just like the other intense scans, however this command will assume the host is up.
It’s useful when, the target is blocking ping request and you already know the target is up.
Ping scan
Command: nmap -sn <target>
Do only a ping only on the target
Quick scan
Command: nmap -T4 -F <target>
Scan faster than the intense scan by limiting the number of TCP ports scan to only the top 100 most common TCP ports.
Quick scan plus
Command: nmap -sV -T4 -O -F –version-light <target>
Add a little bit of version and OS detection and you got the Quick scan plus.
Quick traceroute
Command: nmap -sn –traceroute <target>
Use this command option when you need to determine hosts and routers in a network scan. It will traceroute and ping all hosts defined in the target.
Regular scan
Command: nmap <target>
This command means it will issue a TCP SYN scan for the most common 1000 TCP ports, using ICMP Echo request (ping) for host detection.
Slow comprehensive scan
Command: nmap -sS -sU -T4 -A -v -PE -PP -PS80,443 -PA3389 -PU40125 -PY -g 53 –script “default or (discovery and safe)” <target>
In the Target filed, if you want to gather information of only one IP address, we can just enter that address or you want to gather information of the domain just enter that. We can also enter a range like we did with netdiscover like 198.168.1.1/24.
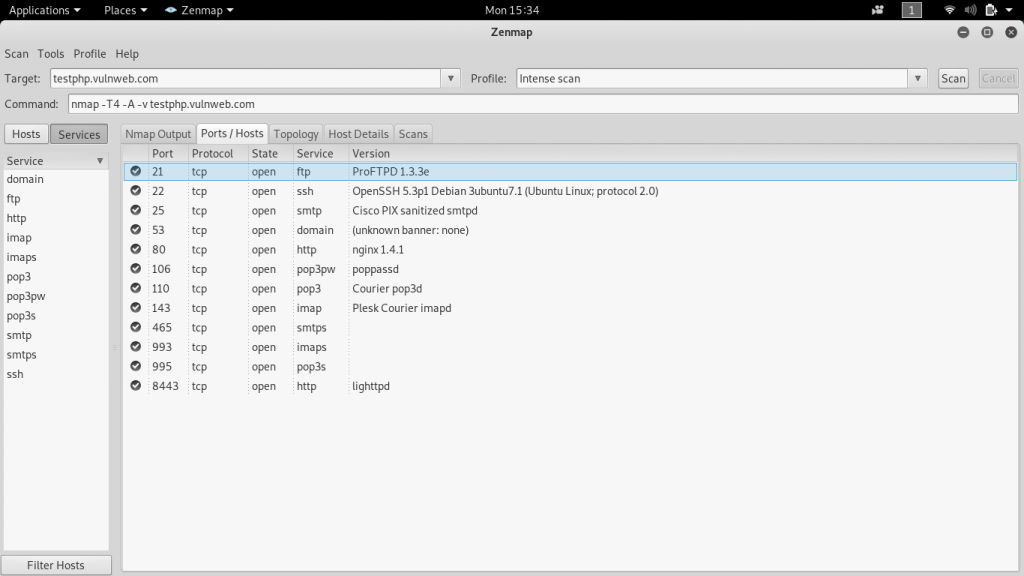
We are going to enter the domain testphp.vulnweb.com and profile is Intense scan.
The Intense scan Should be reasonable quick, scan the most common TCP ports. It will make an effort in determining the OS type and what services and their versions are running.
Here is a picture of a scan in Zenmap software.
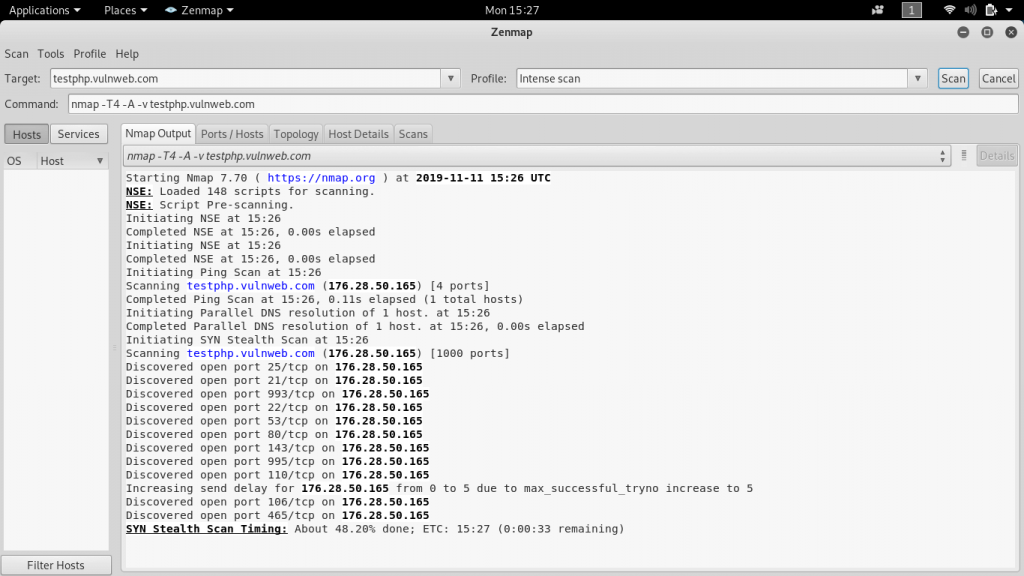
Here is the picture of the output, which we get as a result of intense scan nmap output.
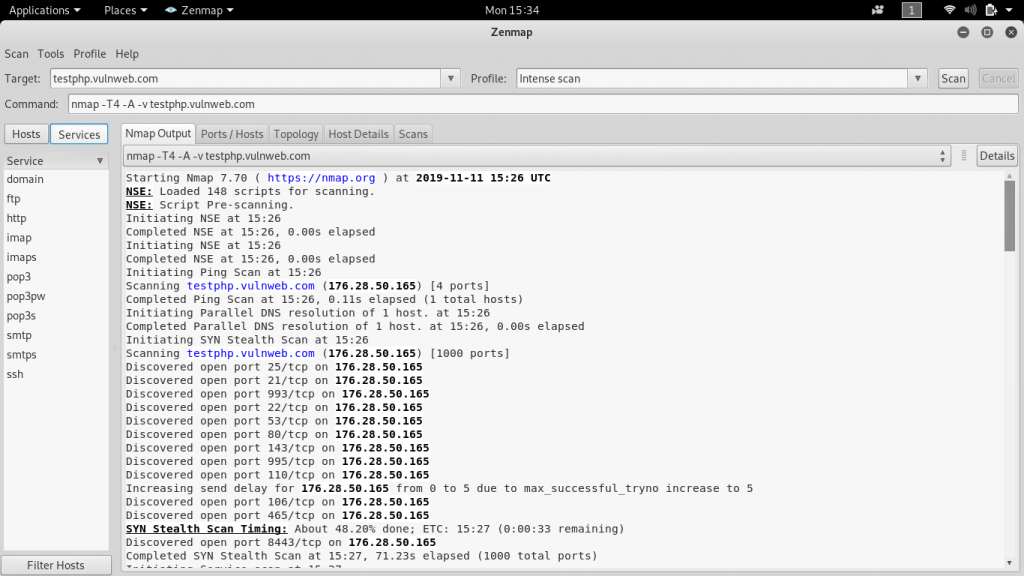
Ports/Hosts scan result