Today, we are demonstrating tutorial on Open-source intelligence Information Gathering suite TheHarvester.
Please check the POC Video at the end of the article.
It aims to collect emails, sub-domains, hosts, employee names, open ports and banners from various public sources, such as search engines, PGP key servers, and the Shodan Computer Database.
It is useful for penetration testers to understand the customer footprint on the Internet and useful for anyone who wants to know what an attacker can see about their organization.
This software is an effective, simple and easy to use.
The sources supported are:
- Google – emails, subdomains
- Google profiles – Employee names
- Bing search – emails, subdomains/hostnames, virtual hosts
- Pgp servers – emails, subdomains/hostnames
- LinkedIn – Employee names
It is completed with new features like:
- Time delays between request
- Virtual host verifier
- Active enumeration (DNS enumeration, Reverse lookups, TLD expansion)
- Integration with SHODAN computer database, to get the open ports and banners
- Save to XML and HTML
- Basic graph with stats
So lets start…
Requirements:
- Kali Linux OS > TheHarvester
It is pre-installed in Kali Linux but there is a case if not installed then use,
git clone https://github.com/laramies/theHarvester.git
>cd theHarvester
>sudo python ./theHarvester.py
or
Open the Terminal and type theharvester and hit enter
Output result are as follow –
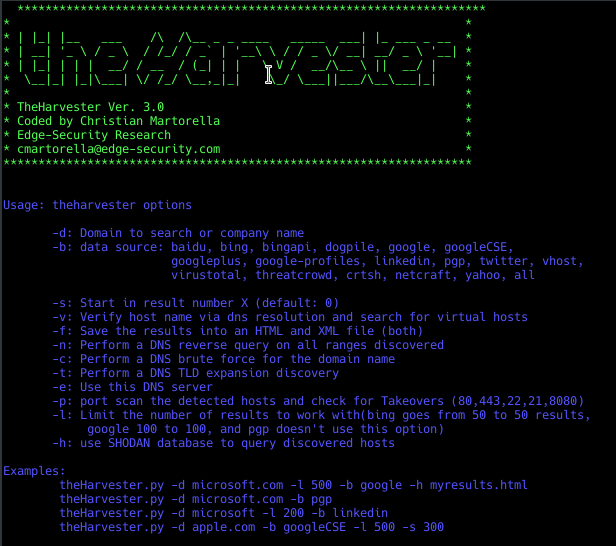
Usage: theharvester options -d: Domain to search or company name -b: data source: baidu, bing, bingapi, dogpile, google, googleCSE, googleplus, google-profiles, linkedin, pgp, twitter, vhost, virustotal, threatcrowd, crtsh, netcraft, yahoo, all -s: start in result number X (default: 0) -v: verify host name via dns resolution and search for virtual hosts -f: save the results into an HTML and XML file (both) -n: perform a DNS reverse query on all ranges discovered -c: perform a DNS brute force for the domain name -t: perform a DNS TLD expansion discovery -e: use this DNS server -p: port scan the detected hosts and check for Takeovers (80,443,22,21,8080) -l: limit the number of results to work with(bing goes from 50 to 50 results, google 100 to 100, and pgp doesn't use this option) -h: use SHODAN database to query discovered hosts Examples: theharvester -d microsoft.com -l 500 -b google -h myresults.html theharvester -d microsoft.com -b pgp theharvester -d microsoft -l 200 -b linkedin theharvester -d apple.com -b googleCSE -l 500 -s 300
For searching email id’s using one search engine
You can simply use the following command
theHarvester -d [url] -l 500 -b [search engine name]
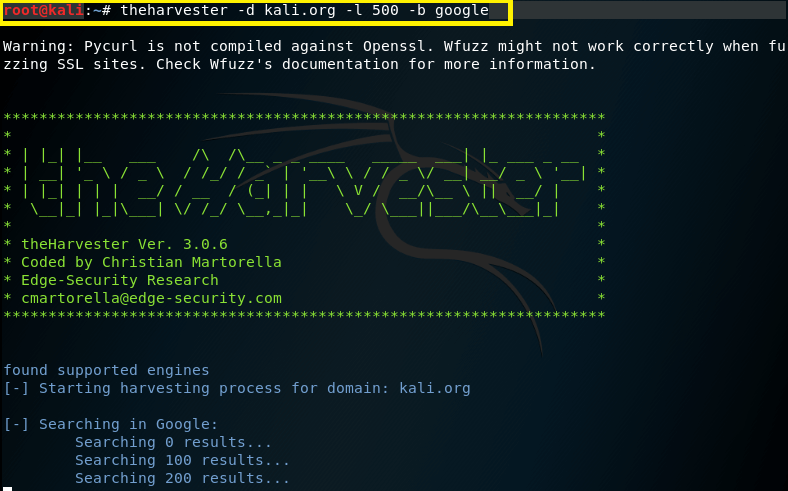
Example : theHarvester -d kali.org -l 500 -b google
Search from email addresses from a domain (-d kali.org), limiting the results to 500 (-l 500), using Google (-b google)
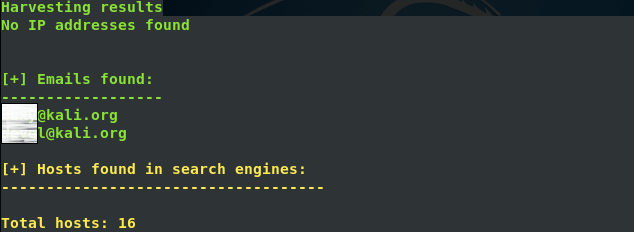
Result we get from the above command
Command for get all the information of the website
theHarvester -d [url] -l 500 -b all
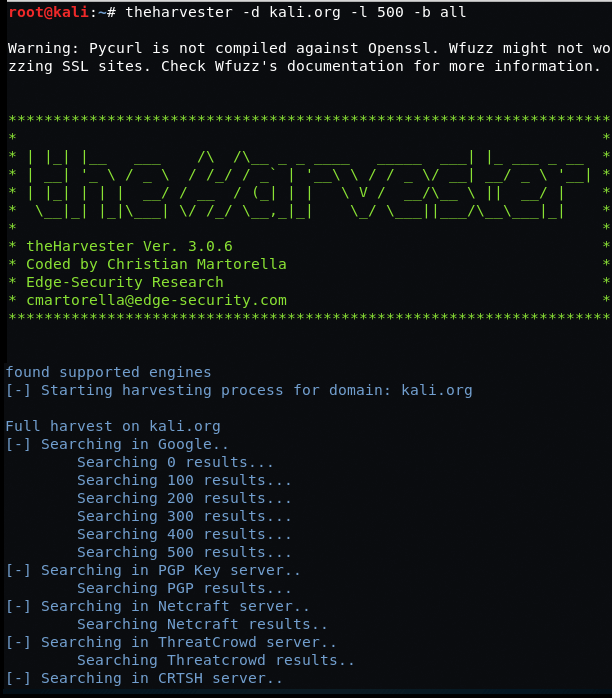
Example : theHarvester -d kali.org -l 500 -b all
Search from email addresses from a domain (-d kali.org), limiting the results to 500 (-l 500), using all (-b all)
To save the result in HTML file you can use -f filename command should be
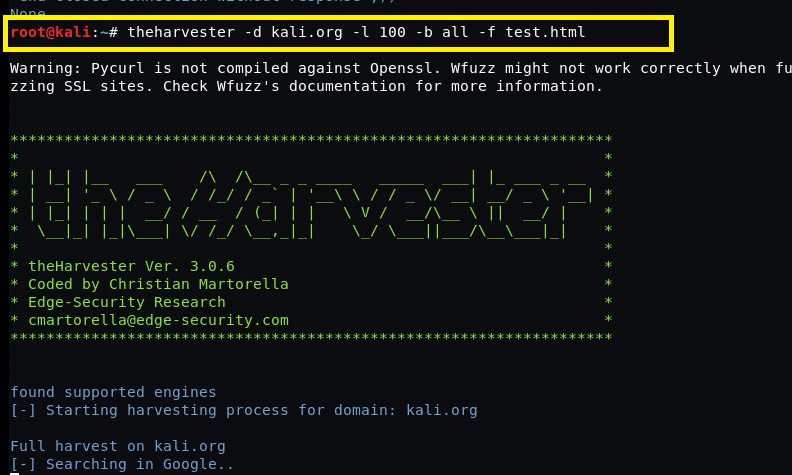
theHarvester -d [url] -l 100 -b [all] -f [file name]
Example : theHarvester -d kali.org -l 100 -b all -f test.html
Search from email addresses from a domain (-d kali.org), limiting the results to 100 (-l 100), using all (-b all) for save the result in the form of HTML (-f test.html) test is a file name
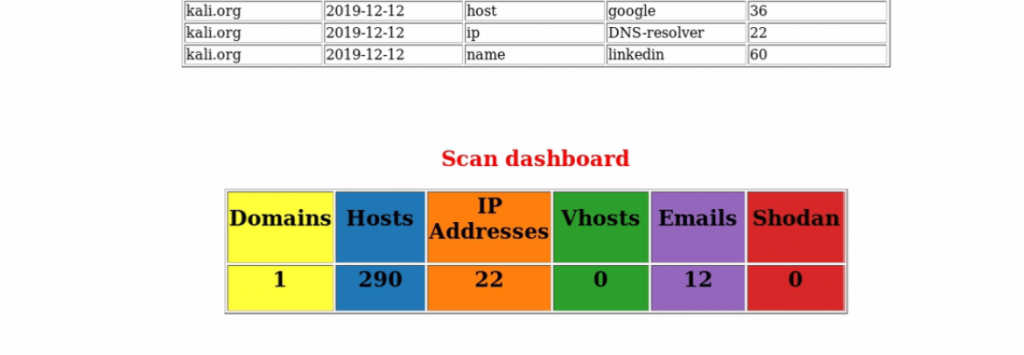
Watch the POC