SQL Injection found in Sophos Firewall Firmware, which has been Fixed now.
Sophos is a British security software and hardware company. Sophos develops products for communication endpoint, encryption, network security, email security, mobile security and unified threat management.
According to Sophos, on 22 April, the company server got malicious attack on its XG Firewall management interface.
The vulnerability affected all versions of XG Firewall firmware on both physical and virtual firewalls. All supported versions of the XG Firewall firmware / SFOS received the hotfix (SFOS 17.1, 17.5, 18.0). Customers using older versions of SFOS can protect themselves by upgrading to a supported version immediately.
Sophos commenced an investigation and the incident was determined to be an attack against physical and virtual XG Firewall units. The attack affected systems configured with either the administration (HTTPS service) or the User Portal exposed on the WAN zone.
The attack used a previously unknown SQL injection vulnerability to gain access to exposed XG devices. It was designed to download payloads intended to exfiltrate XG Firewall-resident data. The data for any specific firewall depends upon the specific configuration and may include usernames and hashed passwords for the local device admin(s), portal admins, and user accounts used for remote access. Passwords associated with external authentication systems such as AD or LDAP are unaffected. At this time, there is no indication that the attack accessed anything on the local networks behind any impacted XG Firewall.
Why is XF Firewall?
XG Firewall’s all-new Xstream architecture delivers extreme levels of visibility, protection, and performance
XG Firewall is the only network security solution that is able to fully identify the source of an infection on your network and automatically limit access to other network resources in response.
Sophos XG Firewall provides unrivaled visibility into risky users, unknown and unwanted apps, advanced threats, suspicious payloads, encrypted traffic and much more.
XG Firewall makes it easy to extend your secure network to employees anywhere.
Sophos Action
The company investigate and determine the components and impact of the attack, Sophos deployed a hotfix to all supported XG Firewall/SFOS versions. This hotfix eliminated the SQL injection vulnerability which prevented further exploitation, stopped the XG Firewall from accessing any attacker infrastructure, and cleaned up any remnants from the attack.
Was my XG Firewall compromised?
The XG Firewall hotfix that Sophos deployed includes a message on the XG management interface to indicate whether or not a given XG Firewall was affected by this attack.
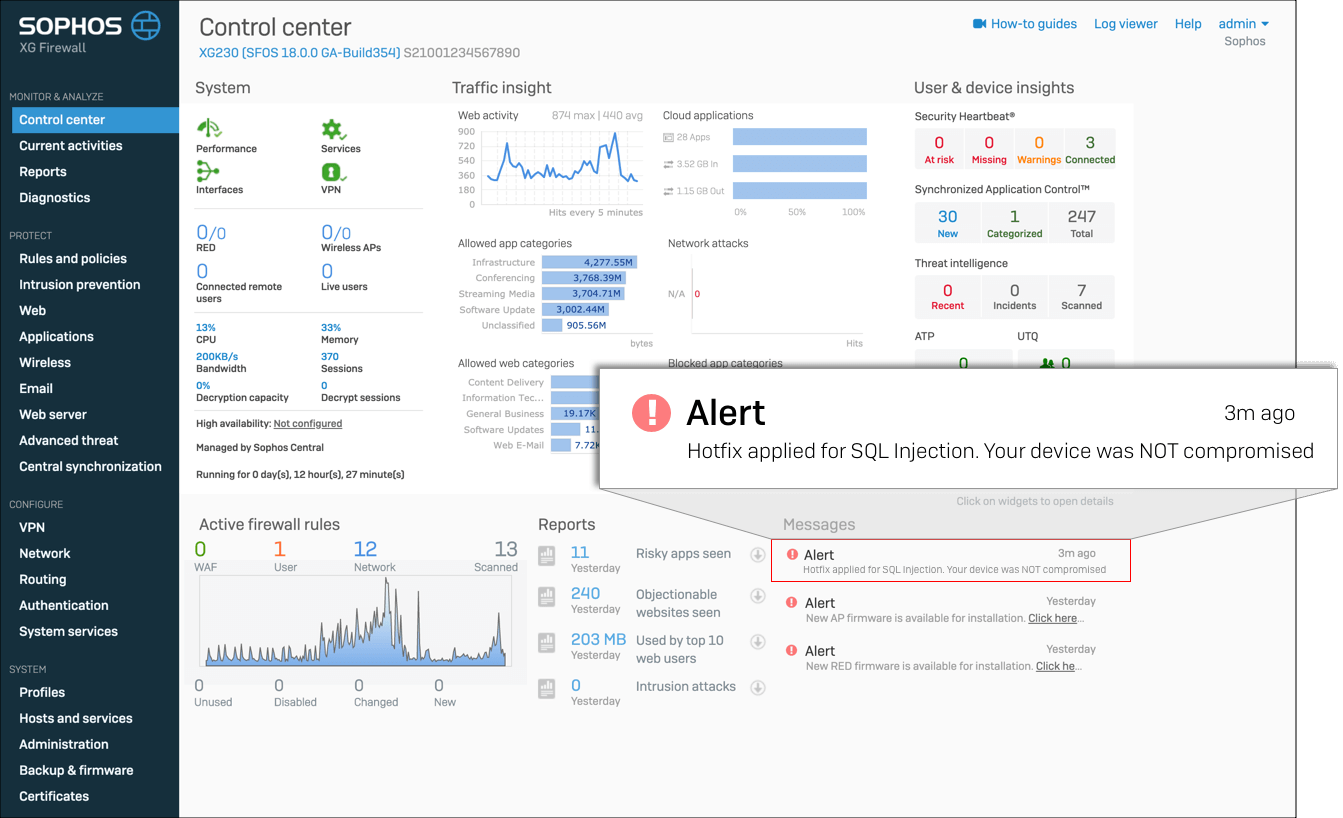
Scenario 1 (Uncompromised):
Hotfix applied to an uncompromised firewall
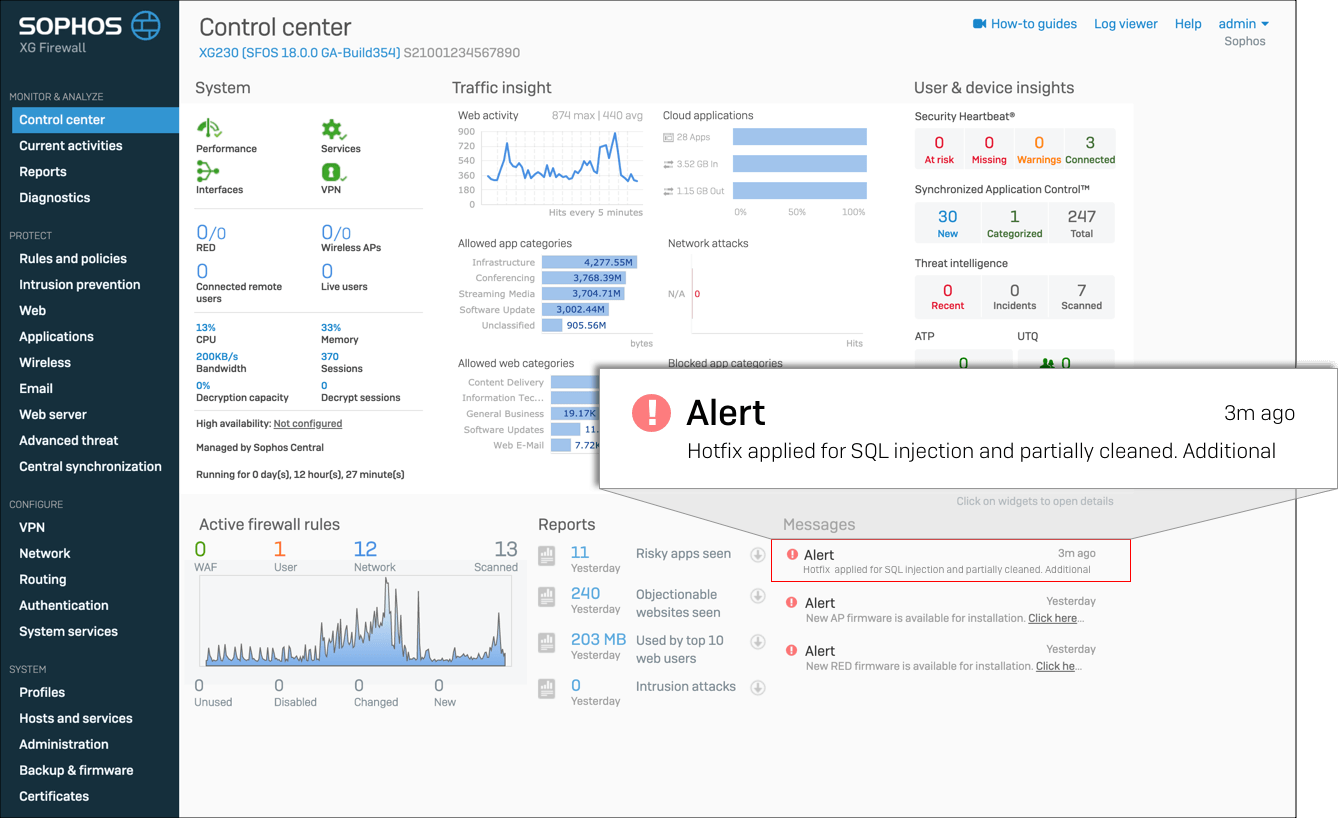
Scenario 2 (Compromised):
Hotfix applied and successfully remediated a compromised firewall
How To Fixed?
Sophos said to its customers. For compromised XG Firewall devices that have received the hotfix, we strongly recommend the following additional steps to fully remediate the issue:
- Reset portal administrator and device administrator accounts
- Reboot the XG device(s)
- Reset passwords for all local user accounts
- Although the passwords were hashed, it is recommended that passwords are reset for any accounts where the XG credentials might have been reused
Timeline
- 2020-04-22 16:00 Attack begins
- 2020-04-22 20:29 Sophos receives report of a suspicious field value in the XG Firewall management interface
- 2020-04-22 22:03 Incident escalated to Sophos internal cybersecurity team
- 2020-04-22 22:20 Initial forensics started
- 2020-04-22 22:44 SophosLabs blocks suspect domains found in initial forensics
- 2020-04-23 06:30 Sophos researchers identify indicators of attack
- 2020-04-23 15:47 Sophos notifies Community of initial mitigations
- 2020-04-23 19:39 Initial attack vector identified as SQL injection attack
- 2020-04-23 21:40 SophosLabs identifies and blocks additional domains
- 2020-04-24 03:00 Telemetry update issued to all XG Firewalls
- 2020-04-24 04:20 Sophos notifies Community of additional mitigations
- 2020-04-24 05:00 Sophos begins design, development, and testing of hotfix to mitigate SQL injection
- 2020-04-25 07:00 Sophos began pushing hotfixes to supported XG Firewalls
- 2020-04-25 22:00 Sophos confirms completion of hotfix rollout to XG Firewall units with auto-update (default) enabled.
How to upgrade sophos xg firewall firmware?
- First Login to your XG Firewall..
- Click on Backup & Firmware in the navigation.
- Under the heading Firmware you will find a list of available versions.
- Click on the upload icon.
- The “Firmware Upgrade/Downgrade” pop-up window will then appear.
- Select the firmware from your computer and click Upload Firmware or Upload & Boot.