Project Freta – A Microsoft Project To Detect Rootkit Malware For Linux System.
Project Freta is a free, cloud-based offering from the NExT Security Ventures (NSV) team at Microsoft Research that provides automated full-system volatile memory inspection of Linux systems.
Project Freta is opening public access to an analysis portal capable of automatically fingerprinting and auditing a memory snapshot of most cloud-based Linux Virtual Machine’s VMs, over 4,000 kernel versions are supported automatically.
Hyper-V checkpoint files captured from a modern enterprise can be searched for everything from cryptominers to advanced kernel rootkits. This prototype previews an exciting future option for cloud consumers: transitioning from boutique forensic consulting services to automated malware discovery built into the bedrock of a commercial cloud.
According to Microsoft,
We often think about the field of computer security as a field of walls and barriers that keep intruders out. With Project Freta, we invite readers to think not of walls but of sunlight. When attackers build malware that cannot be detected, they gain enormous economic value.
Undetected malware can be continuously re-used:
it is never part of attack reporting, never summons incident responders, and never alerts the victim to a data theft event. The economics of reuse can justify enormous attacker investment in malware non-discoverability. Conversely, once a malware strain is discovered, its value plummets in tandem with its reusability.
Key Benefits
- Detect novel malicious software, kernel rootkits, process hiding, and other intrusion artifacts via agentless operation by operating directly on captured VM snapshots.
- Very easy to use: submit a captured image to generate a report of its content.
- Memory inspection means no software to install, no notice to malware to evacuate or destroy data.
- Designed for automating IR-like discovery tasks directly into a cloud fabric – though volatile memory snapshots captured from an acquisition tool can also be used for bare iron scenarios where virtualization is not available.
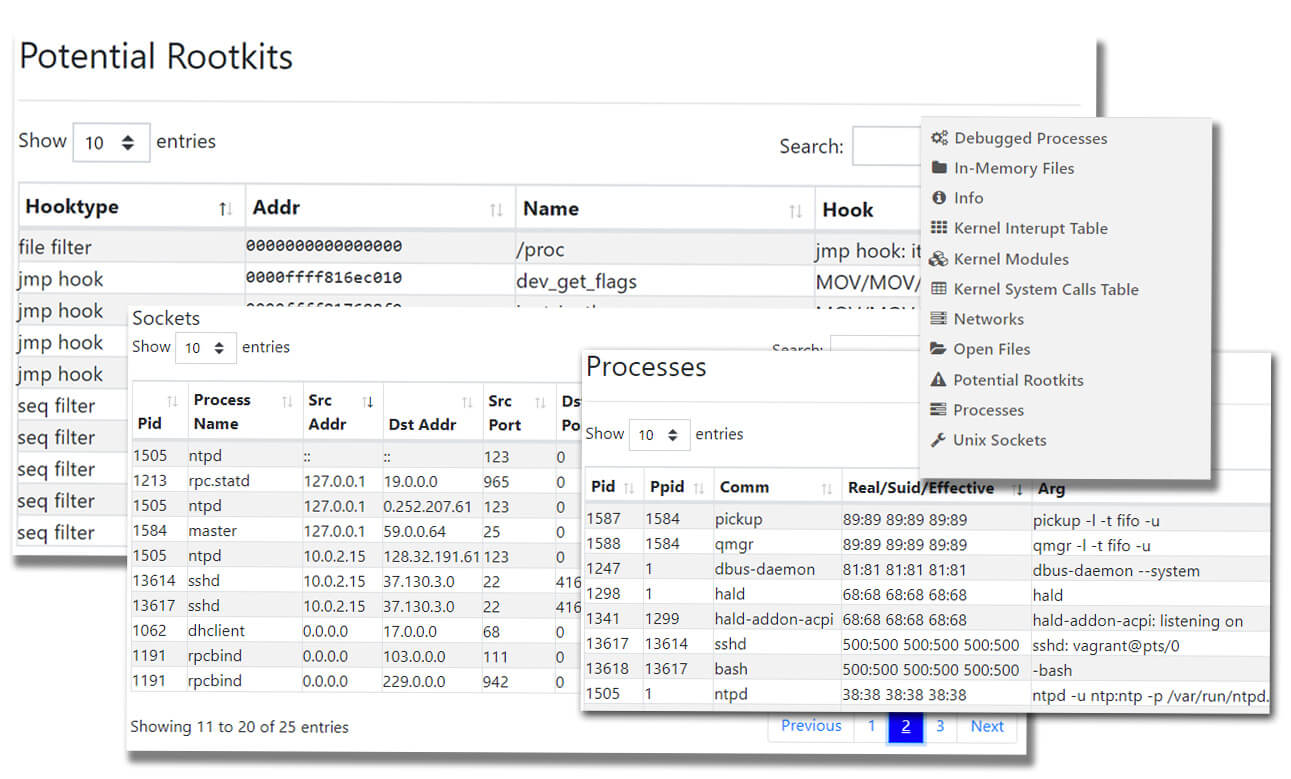
The report contains an enumeration of system objects over the interval during which the sample was taken:
- Global values and addresses
- Debugged processes
- In-memory files
Kernel interrupt table - Kernel modules
- Kernel syscall table
- Networks
- Open files
- ARP table (arp)
- Open sockets
- Processes
- Unix sockets (lsof)
For Project Freta, many of these challenges compounded to make “instant forensics for everyone” a daunting task:
Untouchable Images:
Many existing forensic approaches execute clarifying instructions on the guest, such as copying KASLR keys. Unfortunately, these instructions can tip off malware to a capture event. The requirement not to interact with the target OS, needed to ensure the element of surprise, mandated a forensic imaging technology that was completely “blind.” As a consequence, memory scrambled by security mechanisms such as ASLR needed to be decoded without keys or context.
This task is complex enough for one operating system, and it’s a templating nightmare to support any operating system. Project Freta now supports over 4,000 Linux kernels.
Universal OS Support:
The long-standing forensics requirement that information about the operating system be arrived at a priori needed to be removed. This meant quickly fingerprinting any operating system in the cloud given only a scrambled memory image. We knew from the beginning that, given private symbols, this could be achieved for Windows in a believable way.
So, we chose Linux instead, knowing that the large number of publicly available kernels for Linux would make this problem significantly more difficult. It also meant that a functional result would pay down the technology debt required to build faith in the approach. With Linux behind us, Windows support is on our roadmap.
Cloud Scale:
Automated capture and analysis won’t matter to customers if a day of cloud compute is needed to perform a single audit. To operate on modern cloud enterprises, we knew that the ability to programmatically audit 100,000 machines in a short, cost-bounded time frame was a minimum requirement. This meant architecting from the beginning for batch processing in the cloud, including OS fingerprinting in the performance requirements, and thinking ahead about edge cases such as high-performance-compute VMs with 100+ gigabytes of RAM.
Memory Safety:
We knew that any system designed to hunt for tools fielded by the most well-resourced attackers would itself become a target. Given the history and preponderance of memory-corruption exploits, we made the choice as a team to embrace Rust at the beginning, architecting the entire capability from scratch in Rust from line one and building upon no existing software. This has yielded a high-performance analysis engine for memory images of arbitrary size that also has memory safety properties built in.
The Project Freta analysis engine consumes snapshots of whole-system Linux volatile memory and extracts an enumeration of system objects. Some kernel hooking identification is performed automatically; this can be used by analysts to detect novel rootkits.
The analysis portal is available in prototype form for public use: .
The prototype portal supports many types of memory snapshots as inputs. Currently, only a Hyper-V checkpoint has been evaluated to provide a reasonable approximation of the “element of surprise” necessary to achieve trusted sensing:
- Use the Hyper-V checkpoint feature to produce a VMRS file.
- Convert a VMWare snapshot to produce a CORE file.
- Extract memory from within a running system using AVML.
- Extract memory from within a running system using LiME.
To read full documentation click here











