In this tutorial, we are going to manipulate web application logs to modify items that the user should not usually have access to, such as passwords, permissions or roles which is also known as Mass Assignment.
So, let’s start. You can also check the POC Video at the end of the article.
Requirements
- Burp suite for temper the request
- Web For Pentester II for testing
What is Web For Pentester II?
Web For Pentester II exercise is a set of the most common web vulnerabilities like
SQL injections, Authentication, Captcha, Authorization, Mass Assignment, Randoms issues, Mango DB injection.
You can install Web for Penetester II to Virtual Machine from following link
https://pentesterlab.com/exercises/web_for_pentester_II/
Check the Set up for Web Pentester II [Video]
Start Virtual Machine Web For Pentester II
Type ifconfig for IP address note down the IP address

Type the IP address in your browser which you will get from Web For Pentester II and hit enter.

Now next step is to configure Burpsuite
Go to Browser settings and in the search box type proxy then select open proxy settings > In connection tabs > Lan settings > Tick Use a proxy server for your LAN > (127.0.0.1 port number 8080) then Click ok.

Now open Burp Suite.
In the Burp Proxy tab, ensure “Intercept is off” and visit the Example 1 of Mass Assignment and register your self.
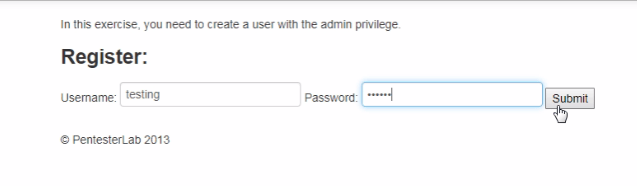
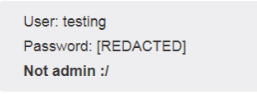
Now Turn on Intercept and then enter the random Username and password in field box and see the interruption.
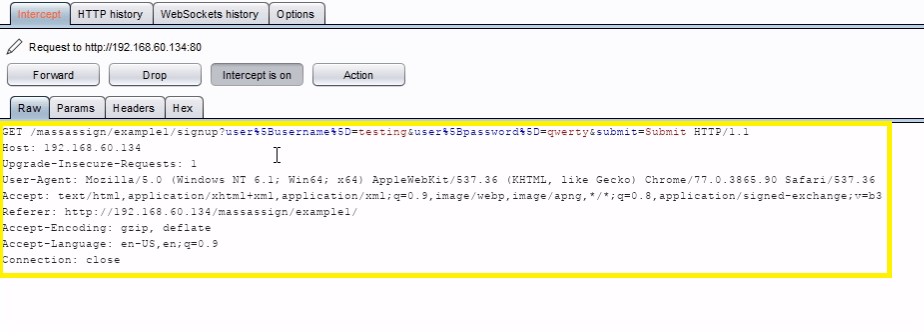
Just go to the params tab on Burpsuit and add a field called user[admin] and set a value to 1 .
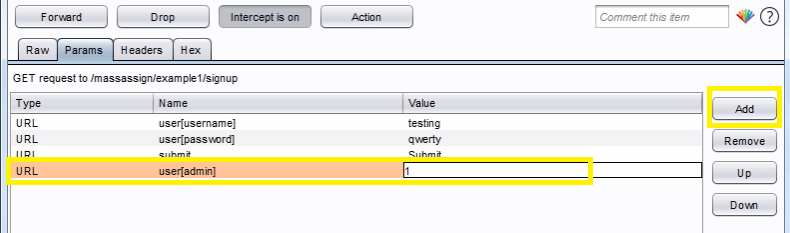
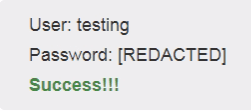
Forward the request, you will get a success feedback from the server.
Example 2 :-In this example we cannot create an account with administrator privileges, but we can update user information and configure it as an admin same trick as example 1 .
For doing this in the Burp Proxy tab, ensure “Intercept is off” and visit the Example 2 of Mass Assignment and register your self .
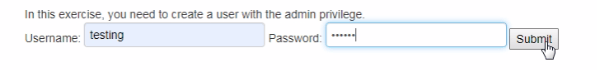
After that click modify your profile.
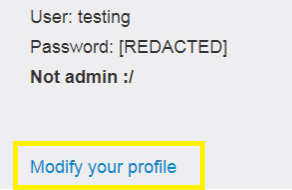
Turn on Intercept and then enter the Enter the username and password in field box and see the interruption.
After that just go to the params tab on Burpsuit and add a field called user[admin] and set a value to 1.
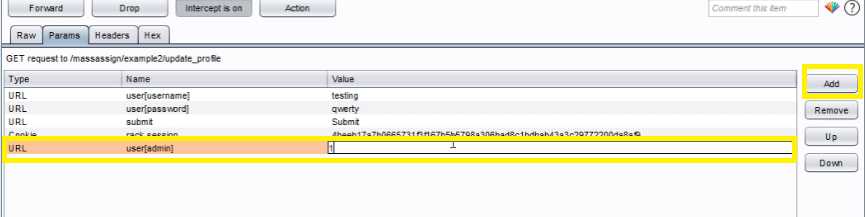
Forward the request, you will get a success feedback from the server.
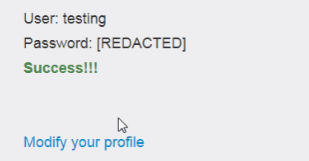
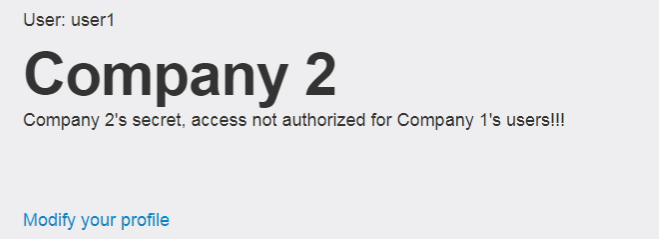
Example 3 :- In this example we can access the info of the company 2 by using the editing function on the account.
For doing this in the Burp Proxy tab, ensure “Intercept is off” and visit the Example 3 of Mass Assignment and register your self .
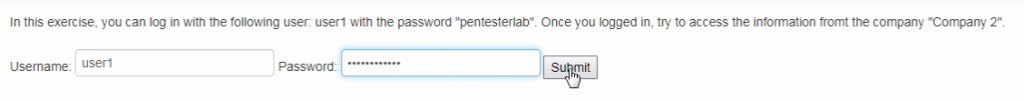
After that click modify your profile.

Turn on Intercept and then Enter the username and password in field box and see the interruption.
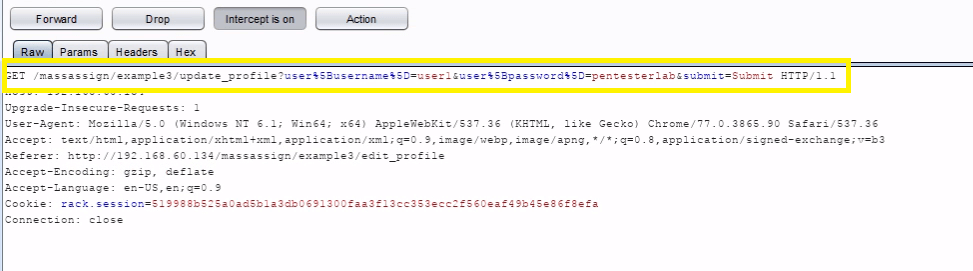
Now just edit the following code :&user%5Bcompany_id%5D=2 to GET request in Burpsuit.
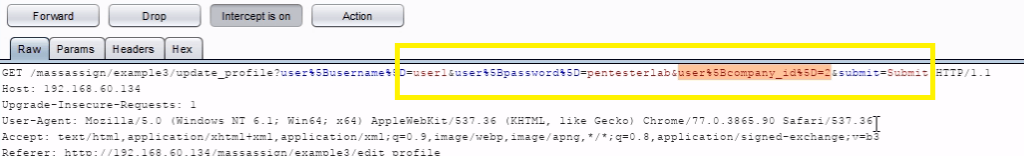
Forward the request, you will get a success feedback from the server company 2 information.
Watch POC
Also See : Burpsuite Spider Feature Working